Crypto continues to gain popularity among both everyday users and the business community, serving as a payment tool, investment vehicle, and reserve asset. The facts speak for themselves:
as of the end of 2024, over 90% of people worldwide had heard of cryptocurrencies, and 42% either currently own or previously owned them;the total volume of stablecoin transactions in 2024 reached $27.6 trillion, surpassing the combined transaction volume of Visa and Mastercard payment networks;by the end of April 2025, institutional investors, including governments, asset managers, and private and public companies, held over 3.16 million BTC.
However, as crypto adoption grows, so do the risks associated with using it. The CP Media team emphasizes the importance of a cautious approach to digital asset security and has compiled a list of basic recommendations to help users avoid the most common mistakes.
Approach to Storing Digital Assets
Storing all assets in a single wallet or service increases the risk of total loss in the event of a hack, technical failure, or user error. In this context, it makes sense for users to diversify asset storage across various types of wallets:
hardware cold wallets are ideal for storing long-term funds that aren’t meant for regular use;software non-custodial hot wallets are suitable for assets that will be used in the near future;custodial hot wallets on trading platforms are helpful for trading or exchange operations.
Investment and reserve funds are best kept in hardware wallets, while only the assets intended for regular use should be transferred to hot wallets.
For business users, multisig wallets, which require multiple private keys to authorize transactions, offer an added layer of security for protecting assets.

Secure Storage of Wallet Access
One of the most common ways users lose access to their wallets is by losing their seed phrase. According to Chainalysis, as of 2022, access to addresses holding around 3.7 million BTC, roughly one-fifth of the total Bitcoin supply, was considered permanently lost.
Recommendation: the seed phrase (private key) generated when creating a wallet must be recorded in a way that minimizes the risk of loss. While recommendations may differ in the details, there’s consensus on the fundamentals, i.e., write down or securely store the seed phrase on protected electronic or physical media, and in multiple copies, and never share your seed phrase with anyone under any circumstances.
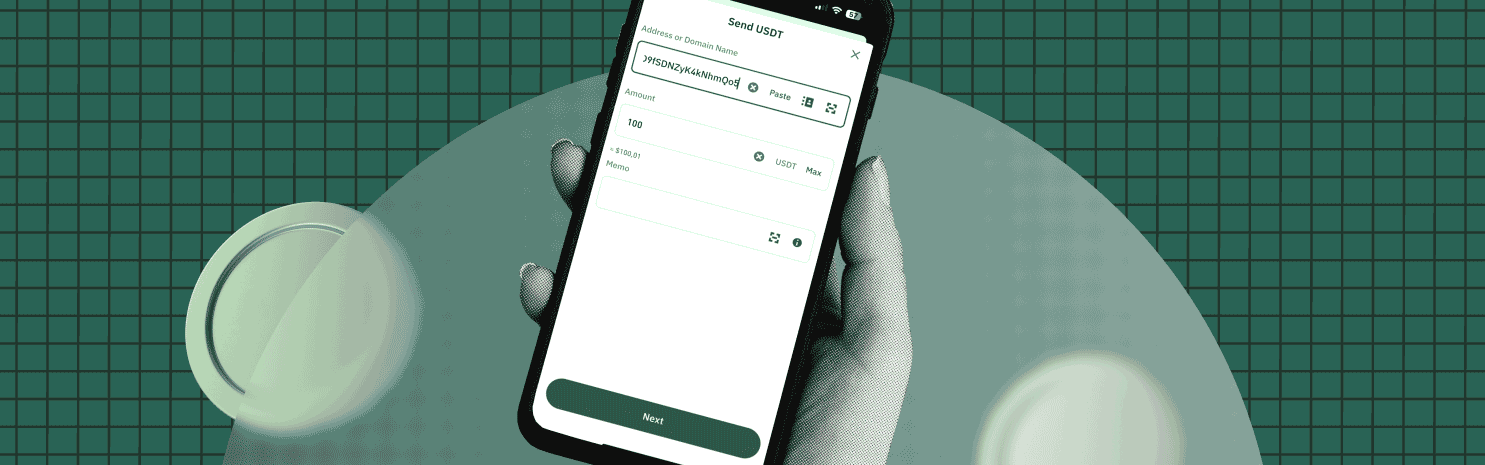
Verifying Crypto Addresses Before Transferring
The irreversibility of blockchain transactions is both a strength and a weakness, since users have no room for error when entering a recipient address.
Common causes of errors include:
mistakes from manually typing the address;clipboard hijacking malware that replaces copied addresses;sending funds to outdated or inactive smart contract addresses;using the wrong network (for example, sending ERC-20 tokens to a Bitcoin address).
A notable example occurred on November 13, 2022, when Crypto.com accidentally sent over 320,000 ETH to crypto exchange Gate. The funds were meant for a new cold storage address but were misdirected due to “human error,” according to the exchange.
Recommendations:
avoid manual entry of addresses — copy/paste or scan a QR code instead;double-check the first and last 6–8 characters of the address before sending;verify the blockchain network and token standard match before initiating the transaction;for large transfers, start with a small test transaction.
It’s also advisable to use wallet and platform features that reduce the risk of mistakes, including QR code scanning, whitelisting trusted addresses, automatic token network validation, and other tools.

Awareness of Current Fraud Methods
It’s hard to call this basic knowledge, but it’s impossible to discuss security without mentioning crypto scammers. It’s important to note that regular users are practically powerless against hackers, as hackers “take by force.” In this context, the only thing users can do is analyze the reliability of specific platforms and software products before starting to use them, as well as apply all available protective measures in practice.
At the same time, fraudsters force their victims to “give voluntarily,” so users can resist them by being vigilant and cautious. However, the key is being informed about the main fraud methods, which today are based on social engineering.

Social Engineering
Social engineering is a general term for fraudulent schemes that allow access to assets or confidential information. The core of social engineering involves psychological manipulation techniques.
Social engineering combines and utilizes all the latest technical solutions available to scammers but primarily relies on users’ inattention, suggestibility, and manipulability. According to the FBI Internet Crime Report, the total losses from crypto fraud committed through social engineering reached $5.8 billion in 2024.
The main mechanism of social engineering is to win the user’s trust and then make them perform necessary actions. Some of the most common social engineering methods include:
Spoofing. A scheme in which the fraudster successfully disguises themselves as someone else by falsifying data and, during communication, gathers confidential info or forces the victim to take certain actions.Pig butchering. It involves building a trusting relationship between the fraudster and their victim through online communication. The goal is to convince the victim to voluntarily give away assets, such as investing in a scam project.Romance scams. A specific example of pig butchering that involves forming romantic relationships via popular social media or dating apps. The communication may last weeks or months to create a strong emotional attachment, after which psychological pressure and manipulation begin to obtain funds.
According to the FBI report mentioned earlier, in 2024, over $70 million was stolen in the U.S. through spoofing, $672 million was lost to romance scams, and $4.57 billion was stolen through pig butchering schemes — approximately 79% of all crypt fraud losses for the year.
There are dozens of social engineering methods, some of which are purely based on psychological manipulation, while others combine psychology with malicious software.
The only way to avoid falling victim to social engineering is vigilance, common sense, and good information hygiene.
With the development of AI solutions and deepfake tools, one must be highly suspicious of strange behavior from online acquaintances, tempting investment offers, emails about sudden inheritances from unknown relatives, suspicious links on favorite forums, unexpectedly sent files in business correspondence, and even video calls from old acquaintances calling from unfamiliar numbers and asking for money.

Phishing Attacks
Phishing is one of the most common forms of social engineering that uses a combination of psychology and malicious software. The goal is to make the victim click on a link and perform a specific action, most often entering their private key. According to CertiK’s 2024 report, the total damage from phishing attacks exceeded $1 billion.
Current phishing attack scenarios involve scammers using various methods to make the victim perform the targeted action, including:
emails with links to phishing websites;fake websites and apps, including those mimicking real popular projects;malicious links on social media, especially on hacked accounts;fake notifications from the “support service” of popular platforms and projects;fraudulent airdrops, and more.
Also, there’ve been recent cases of approve attacks, where fraudulent dApps request permission to manage funds when connected, as well as ice phishing, where users are tricked into signing malicious transactions without needing access to their private keys.
Recommendations:
verify senders of messages through official communication channels;carefully check website addresses and hyperlinks, especially small details in URLs;use multi-factor authentication and other account protection methods.
“Hackers are no longer just hacking wallets or phishing employees. They’re conducting long-term, multi-stage attacks targeting vulnerabilities in people and systems. We must constantly improve our security protocols, just as financial institutions have done for decades,” commented Max Krupyshev, CEO of CoinsPaid, regarding the current challenges facing the crypto business.
Malware and Exploits
Malware and targeted exploits remain one of the key threats to crypto users and infrastructure projects. According to Immunefi, in 2024, the damage from exploits reached nearly $1.5 billion, with a significant portion of the losses coming from DeFi wallet owners who connected to unknown or compromised smart contracts.
Typical attack vectors involve infecting devices with malicious files. The most common scenarios of compromise include:
downloading software or wallets from fake websites;connecting wallets to unknown dApps without checking permissions;installing browser extensions containing malicious code;opening attachments in phishing emails or downloading files from suspicious sources.
Recommendations:
use antivirus software and web security tools like VirusTotal and Hybrid Analysis;only install official versions of cryptocurrency apps, avoiding third-party download sources;conduct regular audits of permissions when working with DeFi protocols, especially approve and transferFrom functions;regularly update software to minimize the risks associated with known vulnerabilities.
It’s also recommended not to use public Wi-Fi networks for cryptocurrency transactions, as they can allow data interception and man-in-the-middle (MitM) attacks.
General Security Recommendations
In summary, here’s a list of basic security recommendations:
When creating crypto wallets, pay special attention to the security of your seed phrases.Diversify the storage methods for digital assets to ensure redundancy and minimize potential losses.Only use trusted platforms and licensed software for cryptocurrency storage, downloaded from official sources, and keep it updated.When conducting crypto transactions, pay close attention to the recipient’s address and ensure the blockchain network and token standard match.Be aware of social engineering methods and pay attention to security issues, both related to the technical tools you use and your own actions online.









